Apr 23, 2021
No image
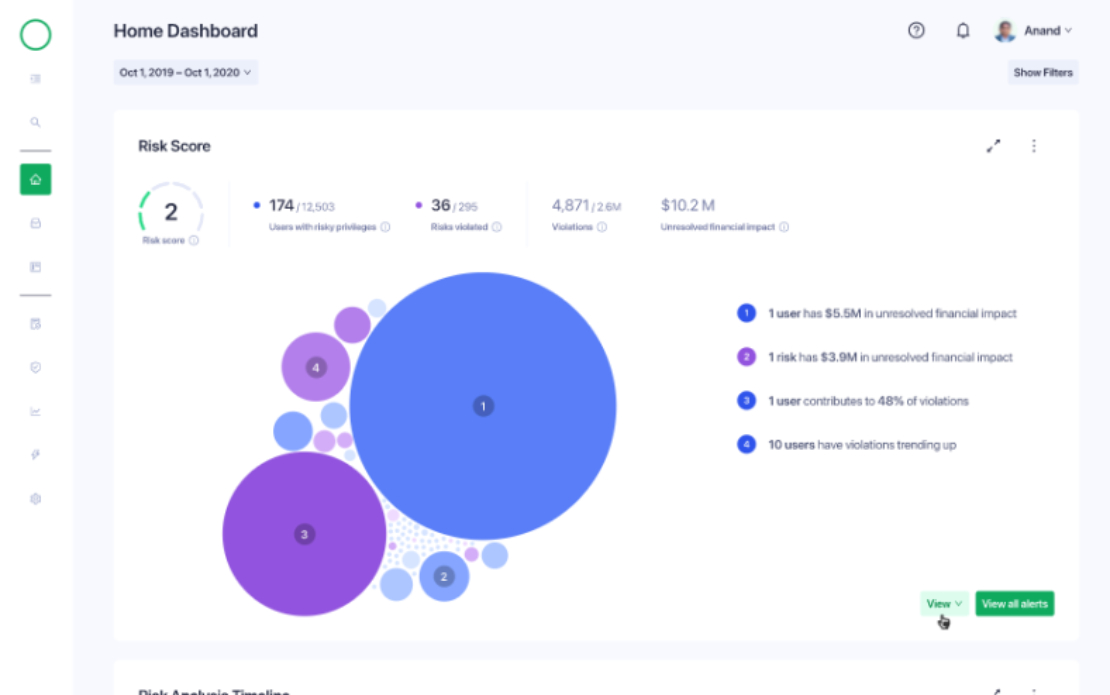
Completed
Securing the Applications that Power the Digital Enterprise
$10,000+
4-6 months
United States
2-5
Service categories
Service Lines
Software Development
Domain focus
Other
Technology
Programming language
Java
Challenge
1. Prevent Unauthorized access:
Design & implement financial & IT General Controls that meet SOX & other compliance requirements.
Run provisioning scenarios with “What-If” analysis before providing access. Allows consistent access control & central oversight.
2 Detect Unauthorized access & usage:
Continuously monitor 100% of privileged activities across all applications in real time.
Monitor third party emergency access.
Reviews & exception management more accurate & timely.
3. Respond:
Revoke privileges or terminate sessions automatically to block malicious behavior.
Focus IT staff on actionable alerts instead of false positives.
Demonstrate compliance with SOX, HIPAA, GDPR & more.
1. Prevent Unauthorized access:
Design & implement financial & IT General Controls that meet SOX & other compliance requirements.
Run provisioning scenarios with “What-If” analysis before providing access. Allows consistent access control & central oversight.
2 Detect Unauthorized access & usage:
Continuously monitor 100% of privileged activities across all applications in real time.
Monitor third party emergency access.
Reviews & exception management more accurate & timely.
3. Respond:
Revoke privileges or terminate sessions automatically to block malicious behavior.
Focus IT staff on actionable alerts instead of false positives.
Demonstrate compliance with SOX, HIPAA, GDPR & more.
Solution
Integration Solutions provided:
> Integration of multiple services and implementation of microservices.
Integration Solutions provided:
> Integration of multiple services and implementation of microservices.
Results
> Covers hybrid and multi-cloud applications
> Workflow Helpdesk Integration
> Location Based Dynamic Access
> Adaptive Authentication down to field level (MFA)
> Inline Transactional Enforcement (block transactions live > based on rules)
> Dynamic Data Masking
> Usage Based Role Recommendation Engine
> Supports over 140 integrations such as Okta, Azure, Servicenow, Aveska, Splunk, SAP etc
> Covers hybrid and multi-cloud applications
> Workflow Helpdesk Integration
> Location Based Dynamic Access
> Adaptive Authentication down to field level (MFA)
> Inline Transactional Enforcement (block transactions live > based on rules)
> Dynamic Data Masking
> Usage Based Role Recommendation Engine
> Supports over 140 integrations such as Okta, Azure, Servicenow, Aveska, Splunk, SAP etc
