How To Protect Mac Computers In a Small Business Company
According to a survey by Symantec, many employees and enterprises use Mac at work. Therefore, the question arises whether the system is safe and whether small businesses should use Mac computers.
You must keep your Mac free from virus and malwares if you work for a small business. Making a backup system is the most effective way to do this because it will enable you to recover in any circumstance. Further, it's simple to let computer security slip when running a small business. But it's crucial to maintain your Mac in prime condition from malwares & antiviruses, especially if you're a business owner who depends on it for dependability. The following are some steps for securing your Mac in a small business company.
1. Set A Firm Password
Make a strong password. A difficult-to-guess password is one that uses a combination of characters, numbers, and symbols. Use a password manager like LastPass or 1Password if you can't remember it.
Put two-factor authentication to use (2FA). By requiring users to enter their login information using two different methods – for instance, by typing in their username followed by the number associated with that device – 2FA adds an extra layer of security.
2. Disable Spotlight suggestions
Go to System Preferences > Spotlight to turn off the suggestions in Spotlight. Then pick "All results" under "Show search results in."
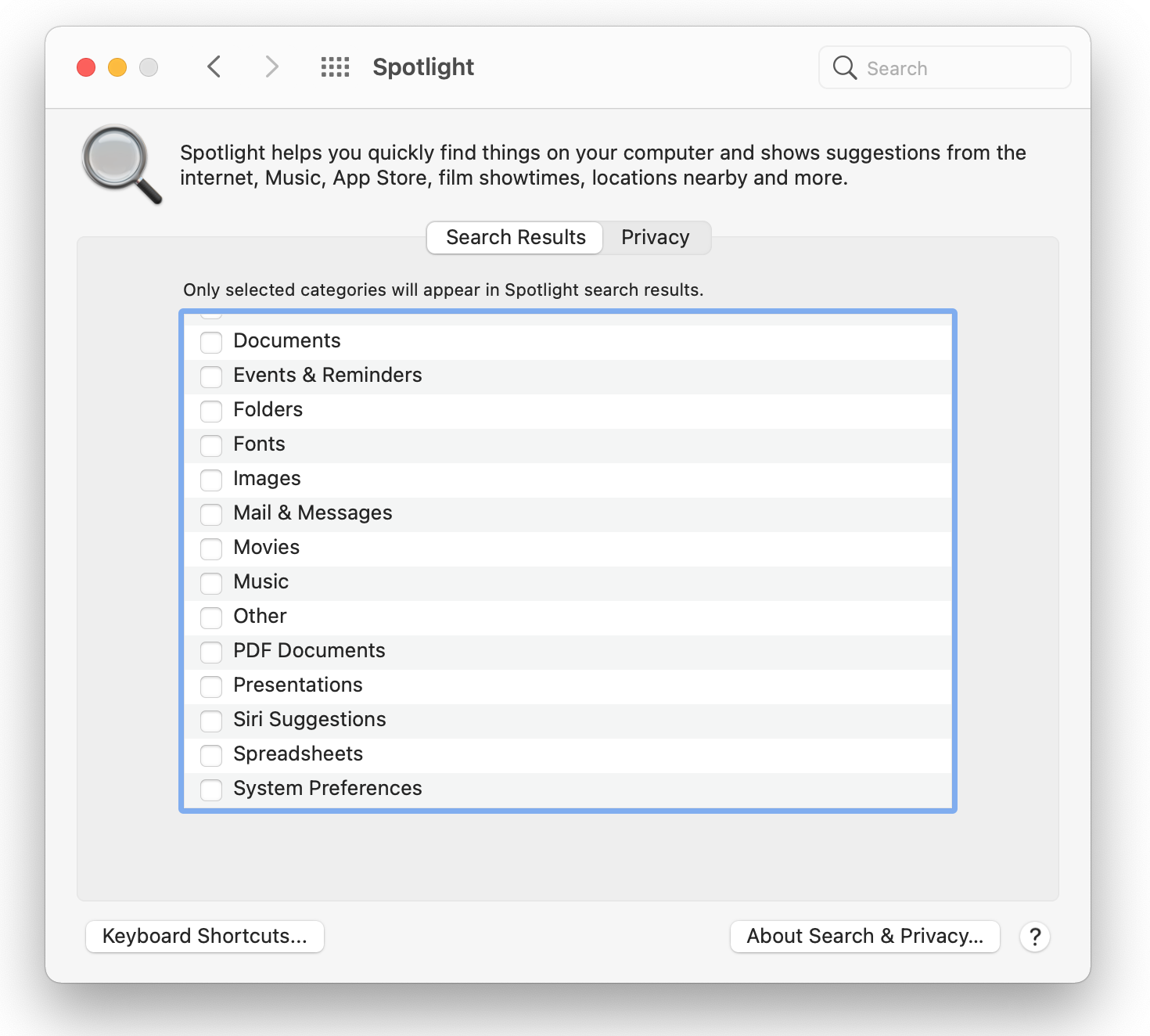
Additionally, you can limit Spotlight's access to specific files by selecting the Plus sign next to the file you want to make invisible to Spotlight. Choosing "Open With" will give you three choices: Windows, Other Programs (which refers to any program), or No Application (which prevents all apps from being able to access that file). Depending on the number of applications you have installed on your computer, you might require more than one of them. All apps will be alerted to the modification as soon as you make it in this paragraph and will instantly update themselves to reflect the change so that when conducting a search for that specific file type, they are no longer visible.
3. Backup Your Mac
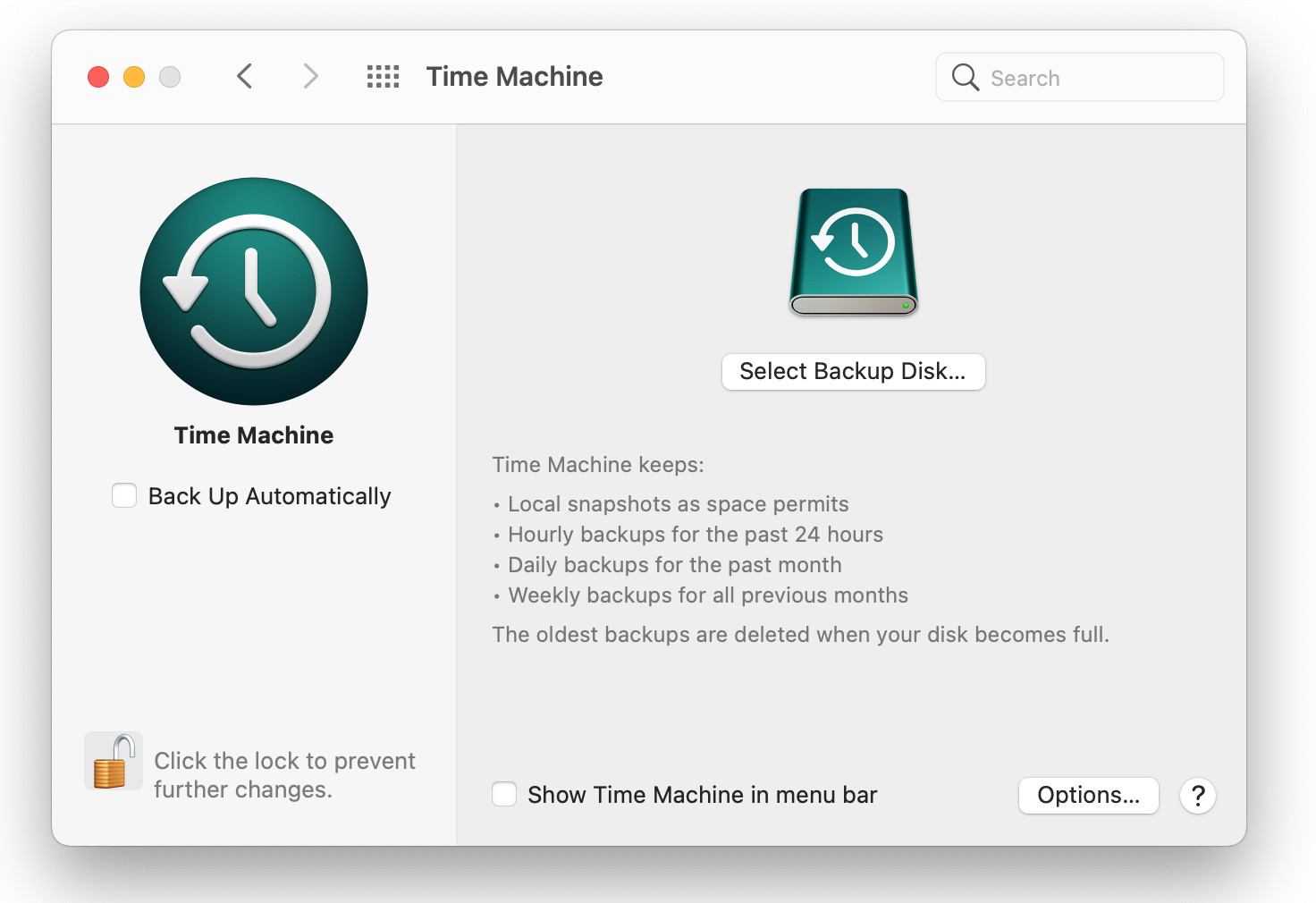
A backup tool called Time Machine is included with macOS. It saves files throughout your computer and works as a set-and-forget solution. In order to make room for new content as photographs and videos accumulate, Time Machine will automatically store the file's oldest version.
- Connect your Mac to an external hard drive. A drive at least the same size as the internal drive in your Mac is required. (Time Machine will, by default, occupy all of the drive's space.)
- Select the backup location and start Time Machine. Toggle the setting from "Off" to "On" in System Preferences > Time Machine after connecting your external drive.
- The drive or volume you want to use for Time Machine can then be selected by clicking the "Select Disk..." button. Time Machine will ask you if you want to use the disc as the location for your backups and will give you the option to password-protect the backups. The storage device must be formatted for Mac OS.
4. Use An Antivirus
Make sure your antivirus software is up to date and installed on all devices if you use a small business. This can help shield your Mac from malware, spyware, and viruses. Utilizing an antivirus tool made exclusively for Macs is the best method to keep your computer secure (and not Windows PCs).
You can also check the VPN service of various kinds and have good knowledge about different types. So, you should use the best VPN for Mac to secure your Mac security as well as to prevent the virus from your Mac too.
To guarantee that your computer is always shielded from malware, spyware, and viruses:
- Make sure your antivirus program is up to date; updates are frequently released, so don't wait until there is one!
- Ensure that your antivirus program is installed on all other devices being used at home or at work.
5. Enable Auto-Updates
Auto-updates are an excellent way to maintain the security and modernity of your Mac. The best aspect is that only the most knowledgeable users will require them; the typical user lacks time to keep up with all of the updates that are released on a daily basis.
Enable auto-updates: To make auto-updates function, you must have a Wi-Fi or Ethernet connection to the internet. If your Mac has Airplane mode turned on, activate it to ensure that this functions properly (this prevents other devices from connecting). Open System Preferences and turn on "Download updates but let me decide whether to install them" under Security & Privacy > Automatic Updates. By selecting "Check for available updates" in System Preferences > Energy Saver > Update Settings, you can also activate it.
Uncheck "Download recommended updates" under App Store & Updates in System Preferences if you don't want any software to be installed on your computer without your consent – for instance, downloading a new version of Firefox or Safari – before you click on an icon (or any other app store).
6. Create a non-admin account
Make a non-administrator account.
Use this account to access email and browse the web. You can use it for system administration as well, but be sure to keep track of what's happening with your other accounts so that, in the event that one is compromised, you can also find out how things stand with those other accounts.
Ensure that every employee is aware of their rights under the GDPR (General Data Protection Regulation).
7. Security Management
Firewall enabled, Auto-Login turned off
Don't use the same password for matching services or applications; instead, use strong passwords. Consider using a new password for each account if you must use the same one for numerous accounts. If someone were to obtain access to one of your accounts and then steal or guess at other people's passwords in order to gain access to additional data kept on their PCs, this would assist in protecting your data (or even phones).
When possible, utilize two-factor authentication, which requires users to provide an additional piece of information in addition to their username and password when accessing their accounts from other locations. Generally, a code provided through a text message or push notification
8. Clear Caches And Cookies
- Go to the settings menu in your browser and select "Clear Caches" to delete the cache.
- Type "Cookie" into your address bar to delete all cookies from every website you visit. A drop-down menu of websites that have installed cookies on your computer will appear as a result (and thus need to be deleted).
- In Chrome or Safari: Go to Safari > Preferences > General tab > Content Blockers section (or Privacy & Security in Settings) > Content Blockers for Mac OS X Mountain Lion and later versions of OS X Mountain Lion; click Manage... button next to Content Blockers section title at bottom left of window; then check the box next to each item you want to be blocked by default when opening any website within Safari.
9. Keep your Location Private
Keeping your whereabouts confidential should be your primary priority. This implies that you won't only use location services for convenience's sake but only when it's required.
When not in use, uncheck the box next to "Use Simple Privacy" in the System Preferences > Privacy > Location Services preference pane.
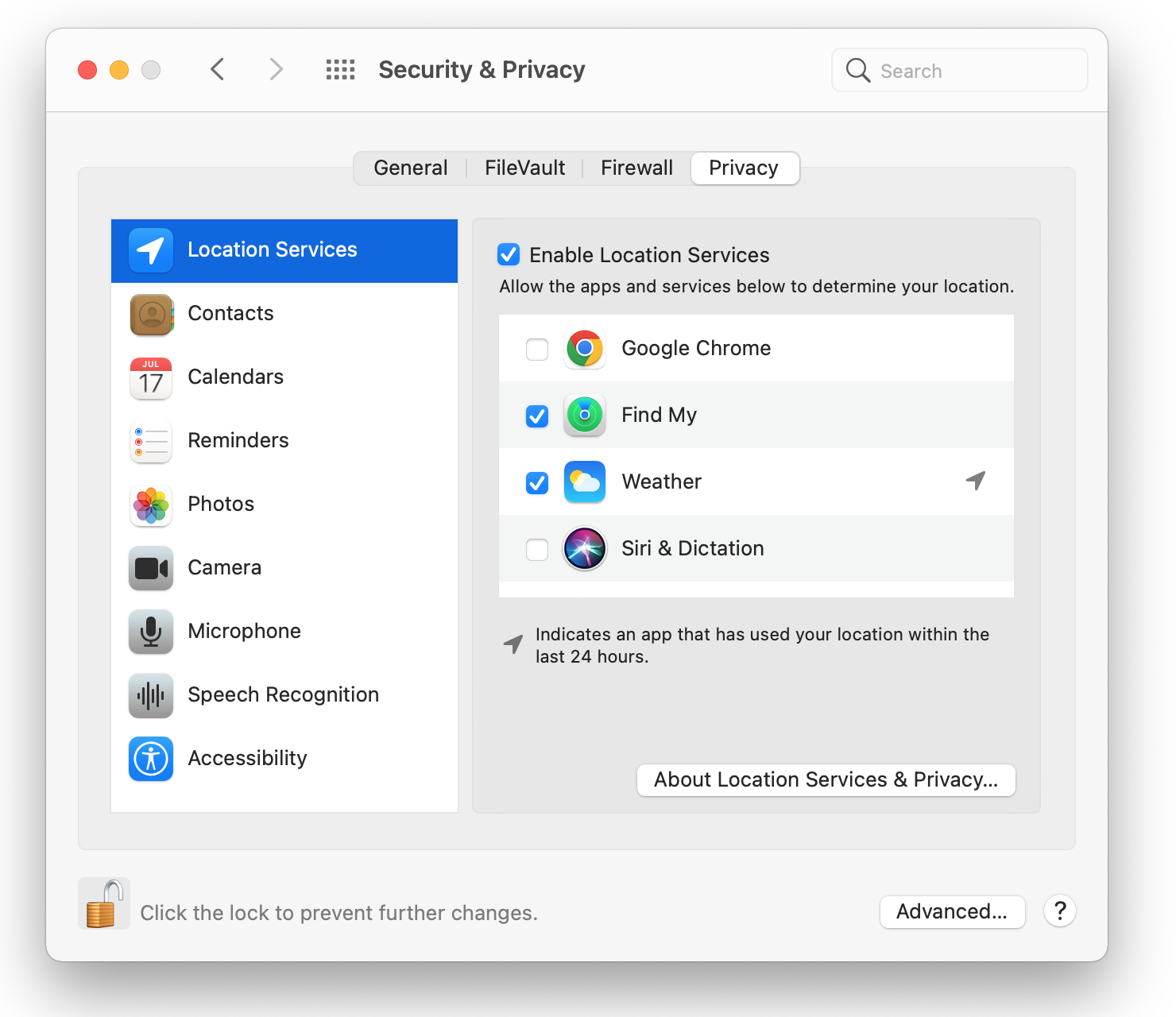
To prevent complications in the future when someone tries to access their own information through another application that does not yet have permission set up properly, make sure that an app has been given instructions if it needs access to your location data (such as Google Maps) before using it. This could lead to issues like crashing or other errors happening.
10. Set Up A Firewall
A firewall is a security device that guards against unauthorized access to your computer. It is a piece of software that keeps track of and manages network traffic, both coming in and going out. To keep hackers from trying to break into your computer via hacking into the network, you can use hardware and software firewalls (i.e., accessing information).
There are numerous kinds of firewalls, such as:
- A Linux-based, open-source firewall system that was first created by the Netfilter Project and later incorporated into the Linux kernel;
- SFW, an advanced application-level packet filtering engine from Sourcefire, offers high performance at a reasonable price;
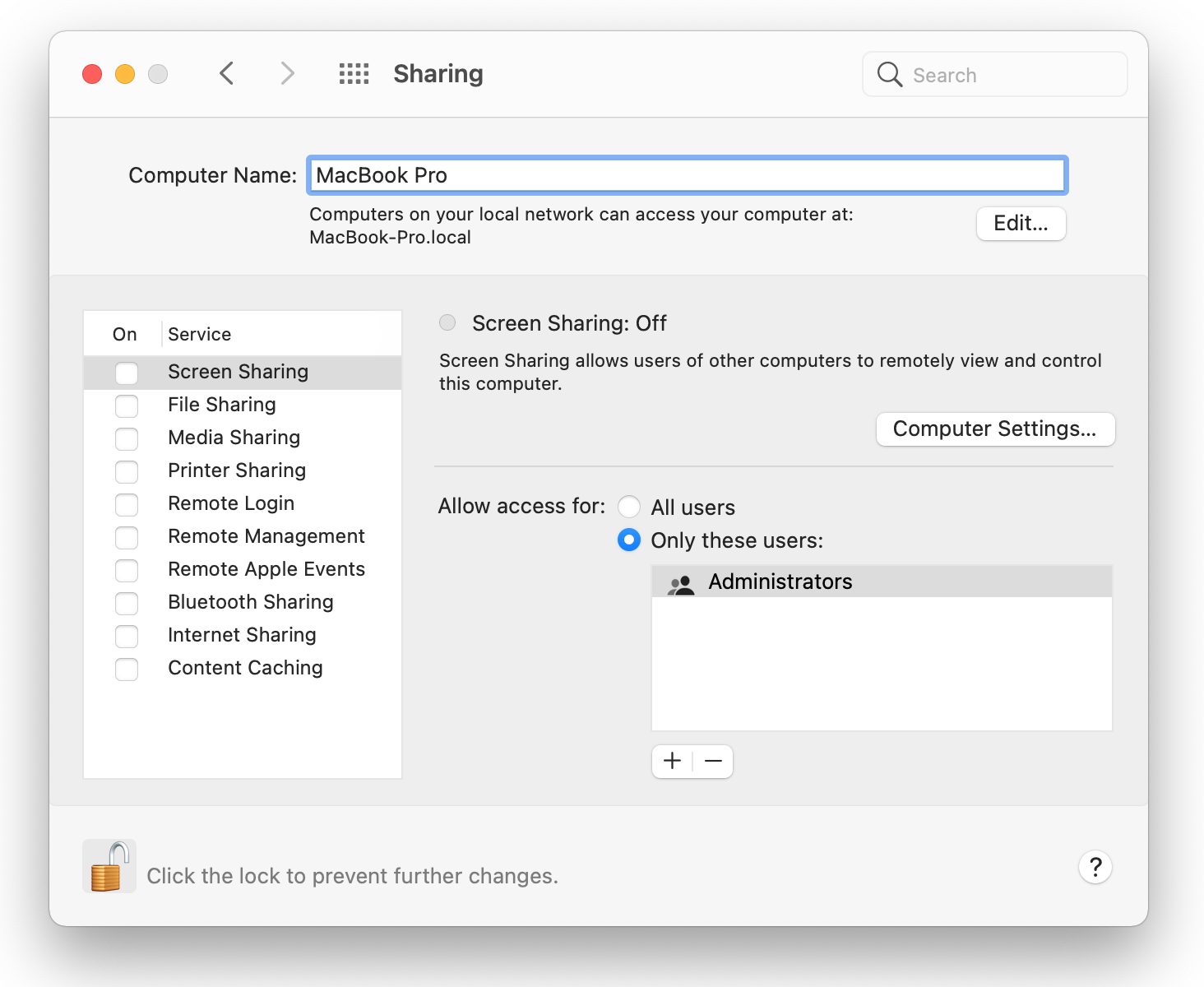
11. Disable Remote Access
A helpful feature of macOS is the ability to access files on your computer remotely from anywhere using a remote connection.
You almost certainly run into at least one malevolent person every day. Additionally, remote access makes things more difficult.
Researchers found a flaw in Apple's business PCs that gave them the power to hack a brand-new Mac as soon as it connected to wifi.
Although convenient, remote access can carry a higher risk. Because of this, businesses implement information security policies that specify when staff members may use it.
Because remote access can reveal your administrator's username and password to anyone with a computer, it's crucial to turn off this capability when not in use. Having a security policy that specifies when employees can use remote access is best practice. (Mac OS users can find information on how to disable it here.)
- Click on the Apple icon in the top-right corner of your screen to launch System Preferences on your MacBook.
- In System Preferences, select the Sharing tab. Enter your Mac administrator password if you get a prompt asking for it.
- Then uncheck the boxes by remote management and remote login. Click the lock once again and input your admin password again to stop further modifications.
- In the top-right corner of the System Preferences window, click the red "X" to close the program.
12. Do Not Fill Your Computer With Unnecessary Software
- Installing unnecessary software is not advised.
- Install software from a dependable vendor you are familiar with and confident in.
- Never share your computer with others or use unlicensed software, as this increases the potential of malware infection and other security risks for your company.
- Installing a program should only be done when absolutely essential (for example, if the program is needed for work). Keep downloaded files off your hard drive unless your Mac has already installed them (such as Adobe Acrobat Reader). This could lead to issues with security updates and other updates that might be required later in order to function as intended after being initially uninstalled!
13. Encrypt your Hard Drive
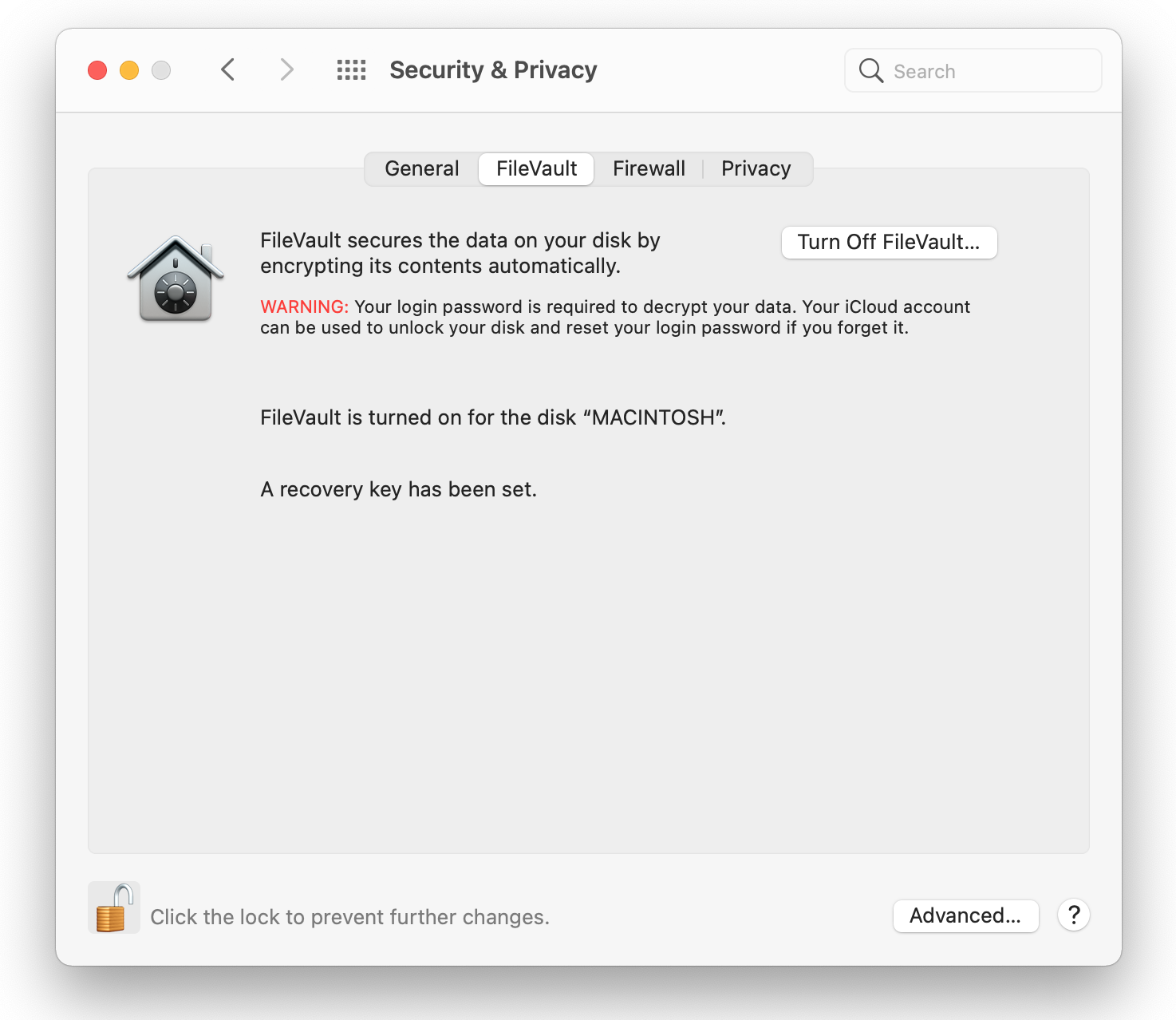
Your safety and the privacy of your recordings depend on encryption. The procedures employed in operating systems like macOS, which encrypt data on your computer's hard drive, are examples of encryption.
- By enabling FileVault, you may increase the security of any Mac that runs OS X.
- Select System Preferences from the Apple menu to modify your computer's settings. Then select Security & Privacy.
- Make sure to select the FileVault tab as a precaution.
- Click "Lock" to lock the tool. Type in your administrator password and username.
- Select Turn FileVault On.
When engaged, the FileVault system asks you to sign in using your account password.
You could notice a message stating that all users must enter their password in order to access the disc if other people have accounts on your Mac. Click the Enable User button and type the user's password for each user. Added user accounts upon FileVault activation.
14. Do Not Open Suspicious Emails Or Attachments
Any questionable emails or attachments shouldn't be opened. Do not even attempt to open an email that you receive from someone you do not know. This poses a risk because if the sender has access to your computer, they might try to infect it with malware or ransomware.
Avoid clicking on links inside emails as well because some websites might have malicious code that, if accidentally clicked on, could infect your system. So, avoid any suspicious emails or attachments because they might be infected with malware or viruses if opened on the wrong computer.
15. Disable Automatic Login
Workers may find it easy to authenticate themselves automatically. To make sure that no unauthorized users are accessing the device, security software must be used with this convenience.
The first step in configuring a new Mac or installing a new version of macOS is to create a user account. By default, when you turn on your pc, that account will be logged in.
Having an active login raises the possibility that someone could steal your laptop while you're away. They may now view all of your files, including strictly confidential emails and client data, with just one click.
Your computer can be set up so that the lock screen loads by default rather than the desktop. Below are some ways to solve the matter.
16. Establish a Backup Solution
Decide on a backup strategy for your Mac.
Backups are important, but if you run a small business, you might not see them that way. The data on your computer could, however, be lost at any time, so it's better to take precautions to safeguard yourself by frequently backing up and ensuring that other machines have access to those backups in case something were to happen to you. You can manually copy items onto an external hard drive or use a program like Time Machine, free, or Carbon Copy Cloner, which costs about $45, depending on your preference. While automatic backup is more work but requires less constant monitoring, manual backup is more affordable but less practical.
Conclusion
Although Macs are excellent tools for small businesses, they also have vulnerabilities. Implementing the recommended best practices described here is the most efficient method to safeguard your Mac. To further safeguard your PC from malware and viruses, you can install a program like Malwarebytes Anti-Malware.
You can take steps to safeguard your Mac in a small business. Making sure that all security measures – and not just one or two – are in place is crucial. In the event that the computer experiences a problem, you will know what to do next.




